Using Google Cloud Identity-Aware Proxy (IAP) with RDP, you will be able to securely connect to your Virtual Instance running Microsoft Windows. Using IAP allows you to also connect to the instance even if it did not have a Public IP address.
- You will need an existing Windows virtual machine ready and running on Compute Engine. You can reference Receipe 5.1 to install a Microsoft Windows Server in Google Cloud.
- In the main menu of the Google Cloud Console, navigate to Networking and click VPC Network.
- Click Firewall in the menu.
- Click Create A Firewall Rule.
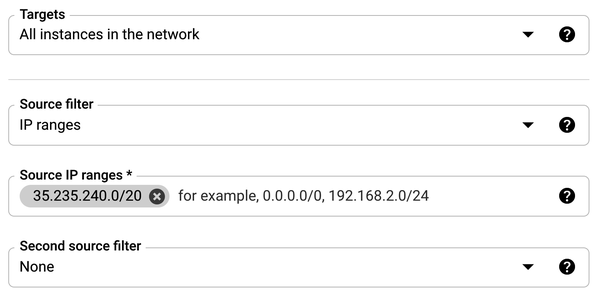
- Enter a name for the firewall rule as
allow-remote-iap. - For the Targets, select All Instances In The Network.
- For Source IP Ranges, enter the following CIDR range:
35.235.240.0/20
The 35.235.240.0/20 CIDR range contains all IP addresses that Google Cloud IAP uses for TCP forwarding.
- Select TCP and enter 3389 to allow RDP in the Protocols And Ports section,
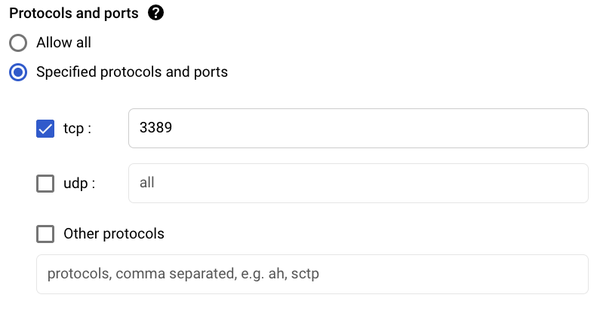
- Click Create.
- Navigate to IAM & Admin > IAM in the Google Cloud Console menu.
- Click Add to allow the groups and users to access IAP TCP forwarding, which will grant them access to connect to the instances in this project.
- For the members, select the groups and or users to whom you want to grant access.
- Select a role and choose IAP-Secured Tunnel User
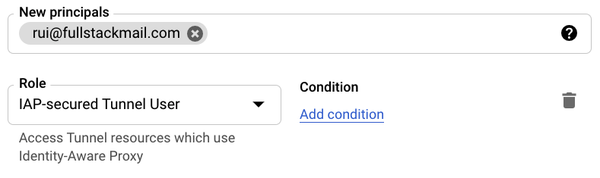
- Click Save.
- Install the IAP Desktop application; you can find the download at https://github.com/GoogleCloudPlatform/iap-desktop. The IAP Desktop application allows you to manage multiple RDP and SSH connections to Google Compute instances securely with IAP.
- Launch the IAP Desktop application and sign-in with the account you granted access to in step 13.
- Select your Google Cloud project
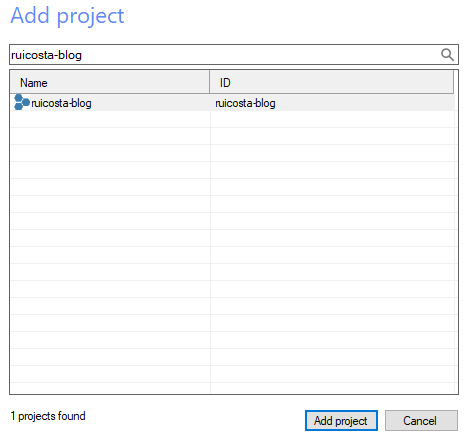
- Once successfully authenticated, you should see your Windows virtual machines listed
Using the IAP Desktop application also provides the following benefits:
- You do not need to expose SSH or RDP to the public internet.
- You can connect to virtual machines that do not have a public IP address.