Cloud Identity’s primary function is to manage identities. However, your organization may already use its own identity provider (IdP), for example, Azure Active Directory (Azure AD).
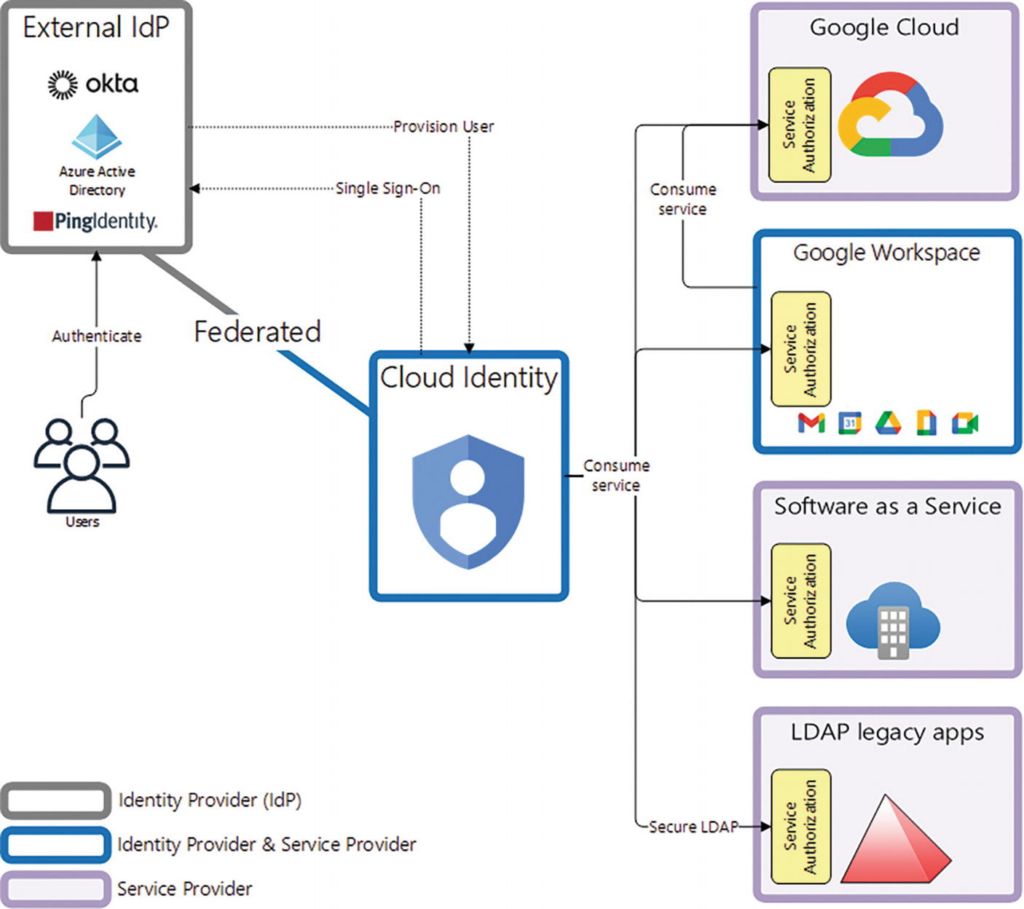
From a user experience:
- Upon requesting the desired service, for example, access to Google Drive, the user is required to sign in to Cloud Identity or Google Workspace with the user’s email address only.
- Next, Cloud Identity (or Google Workspace) redirects the federated user to their organization’s IdP sign-in page.
- Upon successful authentication, the service provider (Google Workspace) performs access control (service authorization) on the requested service (Google Drive). If the service authorization is cleared, then the user can consume the requested service.
In this scenario, it is important to mention the following:
- Google Workspace operates as a service provider because it provides authenticated and authorized users with access to Google Drive.
- The service provider is responsible for managing access control to the requested service, not the IdP, whose function is to perform authentication.
Exam Tip : Cloud Identity and Google Workspace are not limited to an IdP. They can operate as an identity provider and service provider simultaneously.