Three types of IAM roles that you can use:
- Primitive: Coarse-grained roles
- Predefined: Fine-grained roles
- Custom: User-defined roles
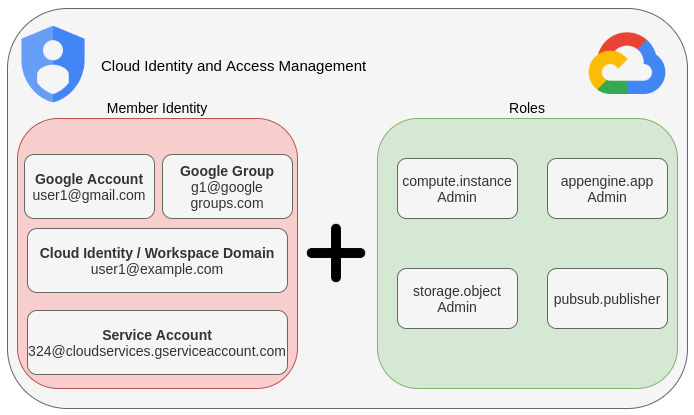
Five types of IAM members:
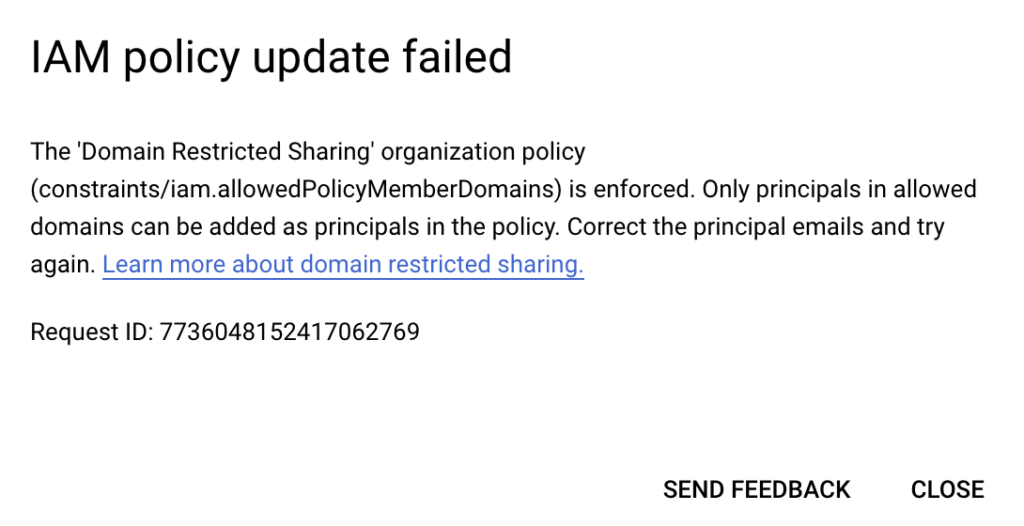
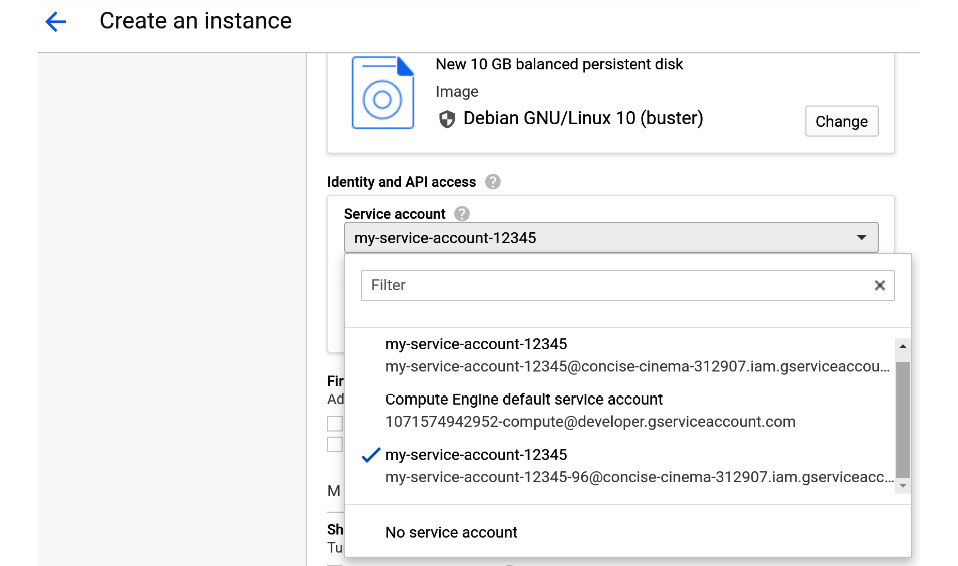
Assigning an IAM service account to a Google Compute Engine instance:
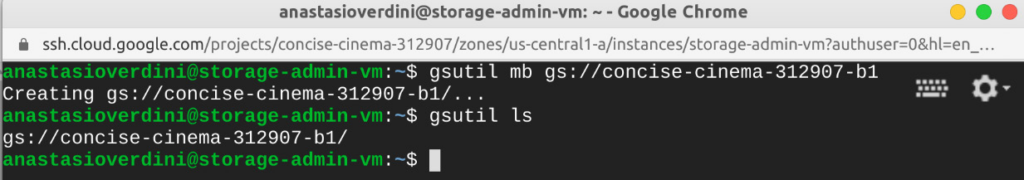
Once the Google Compute Engine is instantiated, you can connect using SSH (Secure Socket Shell) and use the Google Cloud Software Development Kit (SDK) to create and have full control of buckets and objects in Google Cloud Storage. It is important to notice that because the machine has assigned a service account with the appropriate role, you will be able to create a bucket and list files in it.
customStorageRole.yml:
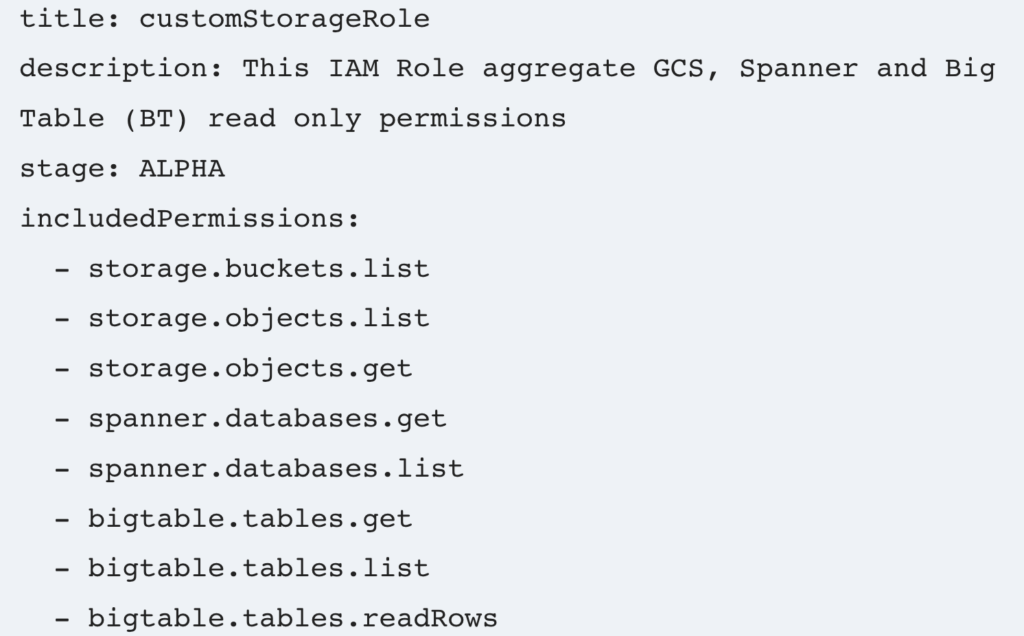
When the custom IAM role has been defined, we can create it using the following gcloud command run in Cloud Shell:
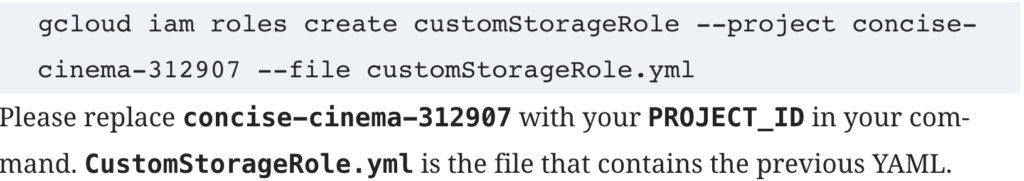
You can now use the custom IAM role as any other role in Google Cloud Platform.
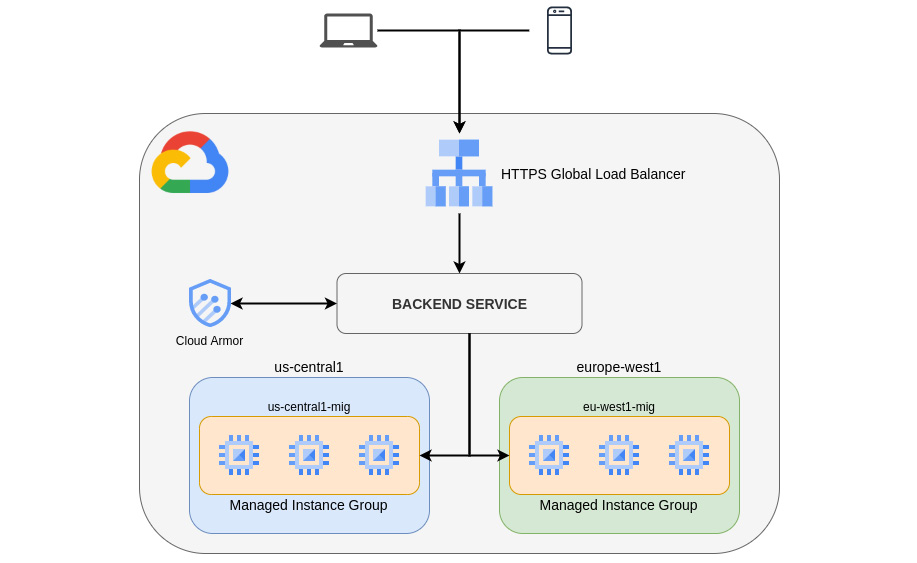
Cloud Armor can only be used attached to a backend service:
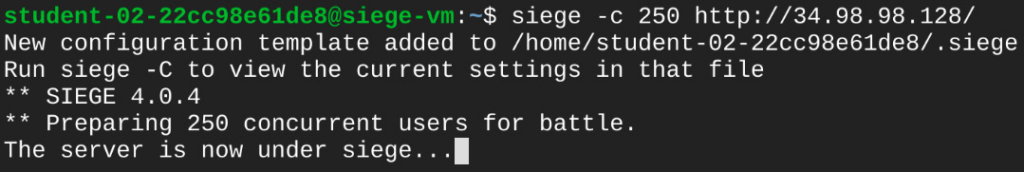
Generating large amounts of HTTP requests:
Network tag could be a way to make this instance a possible target for a firewall rule, or for a route.