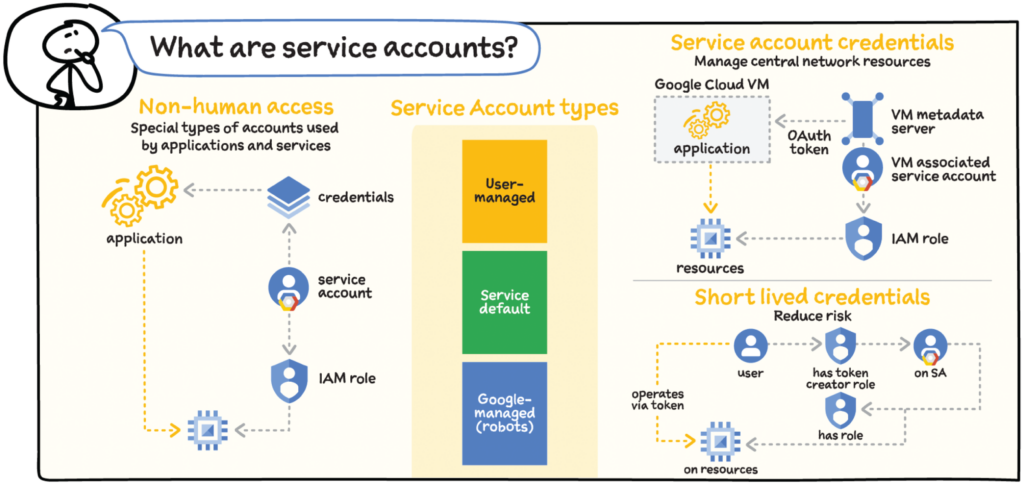
Service accounts are a special type of account used by applications and services. Nonhuman access to Google Cloud APIs and services is usually done through service accounts.
- From a workflow perspective, the default service account is generous with permissions (i.e., Project Editor). It’s a good idea to create app-specific accounts and only grant needed permissions.
- Service accounts can be used for selective applications to apply firewalls. For example: Open port 443 (HTTPS) for VMs for service account ‘webapp-fe’.
- Create service accounts on dedicated projects for centralized management.
- A major security risk related to user-managed keys is keys being compromised, either maliciously or by mistakenly publishing keys by embedding them in code. To help mitigate this risk, rotate keys frequently.
- VPC Service Controls help limit who can access Google Cloud services (which is what service accounts are ultimately for). For example: Access only permitted from on-prem IP ranges (when interconnecting). This greatly minimizes your attack surface.
- Combine service accounts with a proactive approach by using Forseti to alert on old keys that need to be rotated.