Certain Google API based managed services do not use VPC Networks. They use public service endpoints that specifies the network address of an API service.
VM instances that have no external IP addresses can use Private Google Access to reach external IP addresses of Google APIs and services.
For example:
- Cloud Functions
- Cloud Storage
- Cloud Run
- Container/Artifact Registry
- AI Platform – Video Intelligence, Translation, etc.
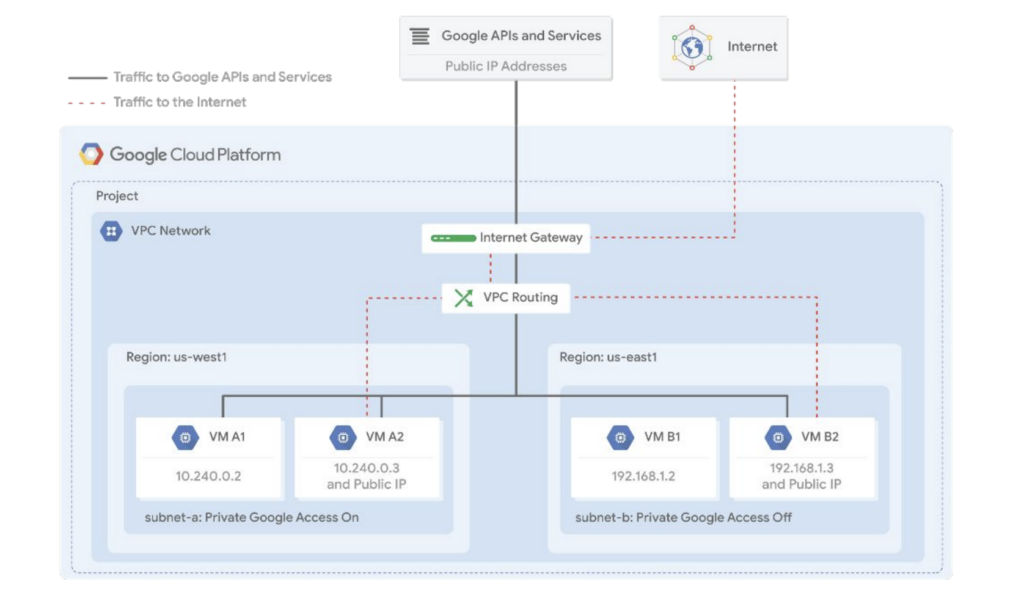
You enable Private Google Access on a subnet-by-subnet basis. As you can see in this diagram, subnet-a has Private Google Access enabled, and subnet-b has it disabled. This allows VM A1 to access Google APIs and services, even though it has no external IP address.
Private Google Access has no effect on instances that have external IP addresses. That’s why VMs A2 and B2 can access Google APIs and services. The only VM that can’t access those APIs and services is VM B1. This VM has no public IP address, and it is in a subnet where Google Private Access is disabled.