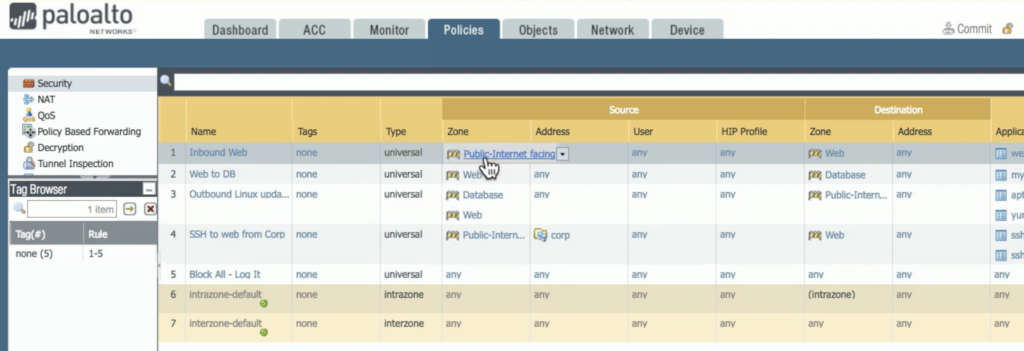
Security rules define whether traffic is allowed or denied between specific zones (e.g., untrusted internet to trusted internal network). The rules are applied in a top-down order, so traffic matches the first rule that applies.
Common fields include:
- Source zone/IP
- Destination zone/IP
- Application: web browsing, email, mysql, ssh, apt-get, yum, etc.
- Action: Allow or deny traffic.
- Logging: Configure whether traffic logs are generated for allowed/denied traffic.